X
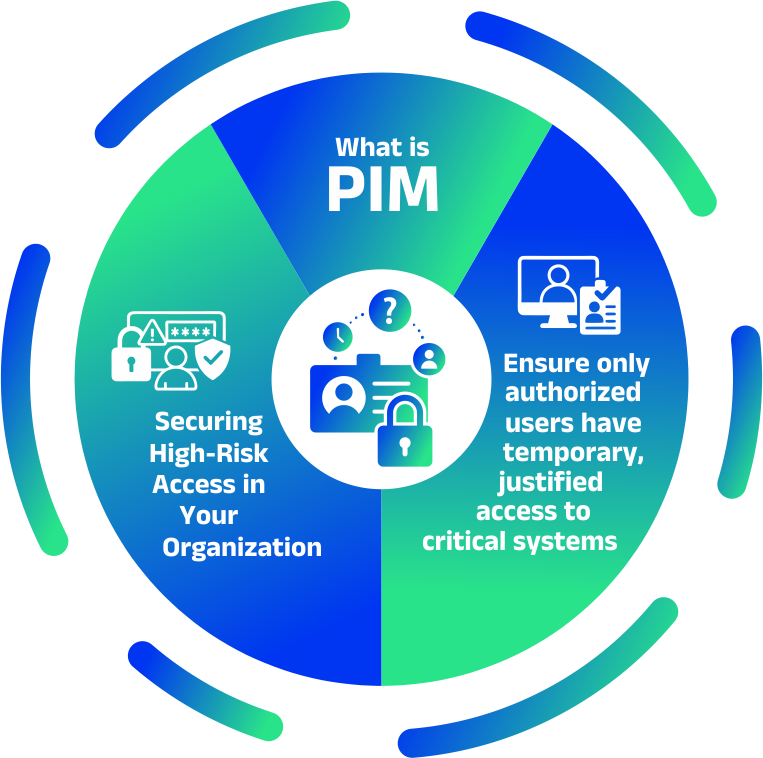
Privileged Identity Management (PIM)
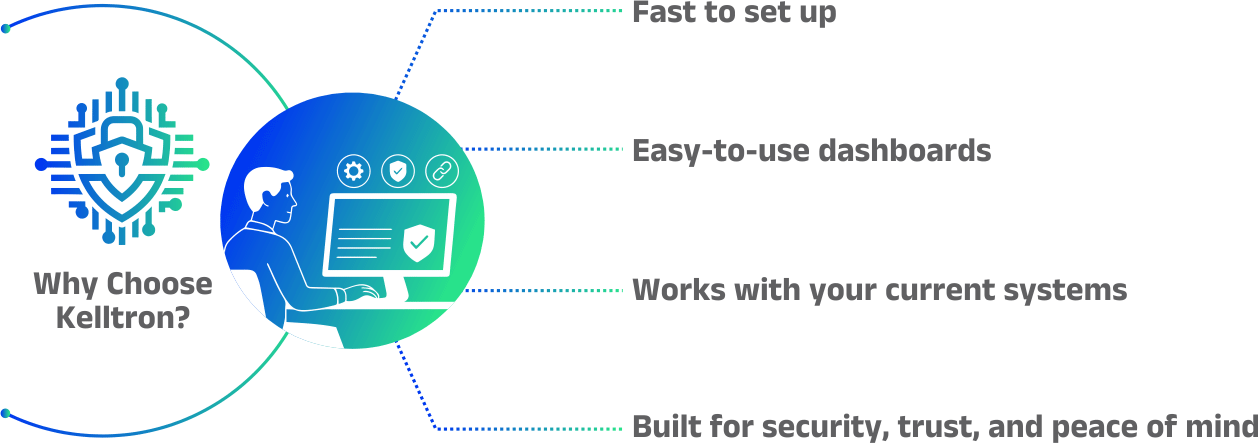
Take full control of privileged access with Kelltron’s intelligent Privileged Identity Management tool, designed to protect, monitor and manage elevated accounts with precision.