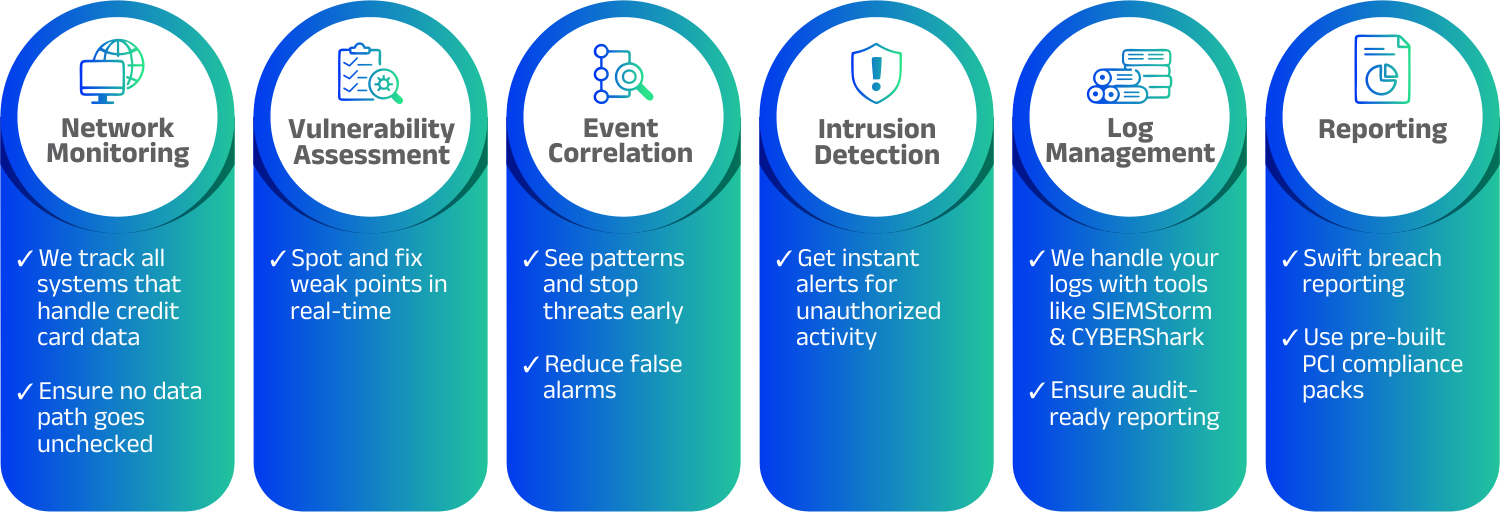
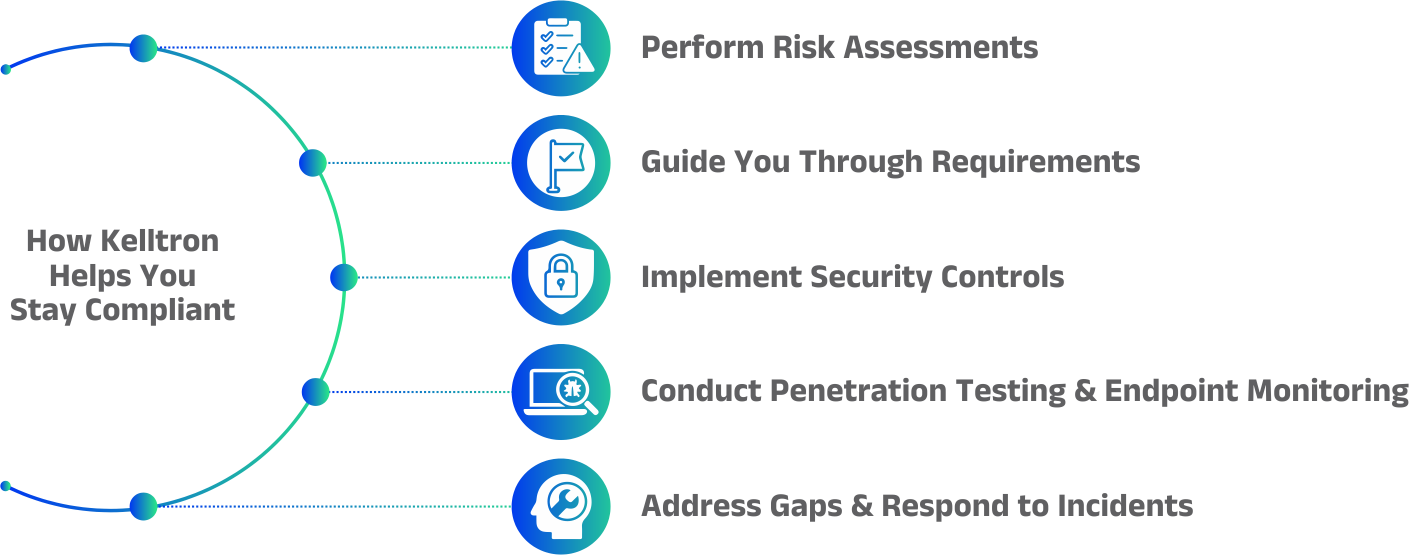
PCI (Payment Card Industry), includes a globally recognized set of security standards to secure payment data and customer information. PCI compliance is mandatory for most businesses to secure networks, continuously monitor, and implement stringent security controls.
Non-compliance can result in significant penalties, reputational damage, and increased security risks. Ultimately PCI compliance is crucial for any organization handling payment data.