
At Kelltron, we turn blind spots into strategic insights. Our Vulnerability Assessment service doesn’t just detect weaknesses, it prioritises what matters and delivers clear, actionable solutions to reduce your attack surface.

Strengthen your security posture with controls aligned to the global gold standard for managing information risks and safeguarding assets.
Ensure secure handling of cardholder data and protect payment environments from fraud, breaches, and compliance penalties.
Achieve and maintain data privacy compliance by identifying vulnerabilities that could lead to unlawful data access or exposure.

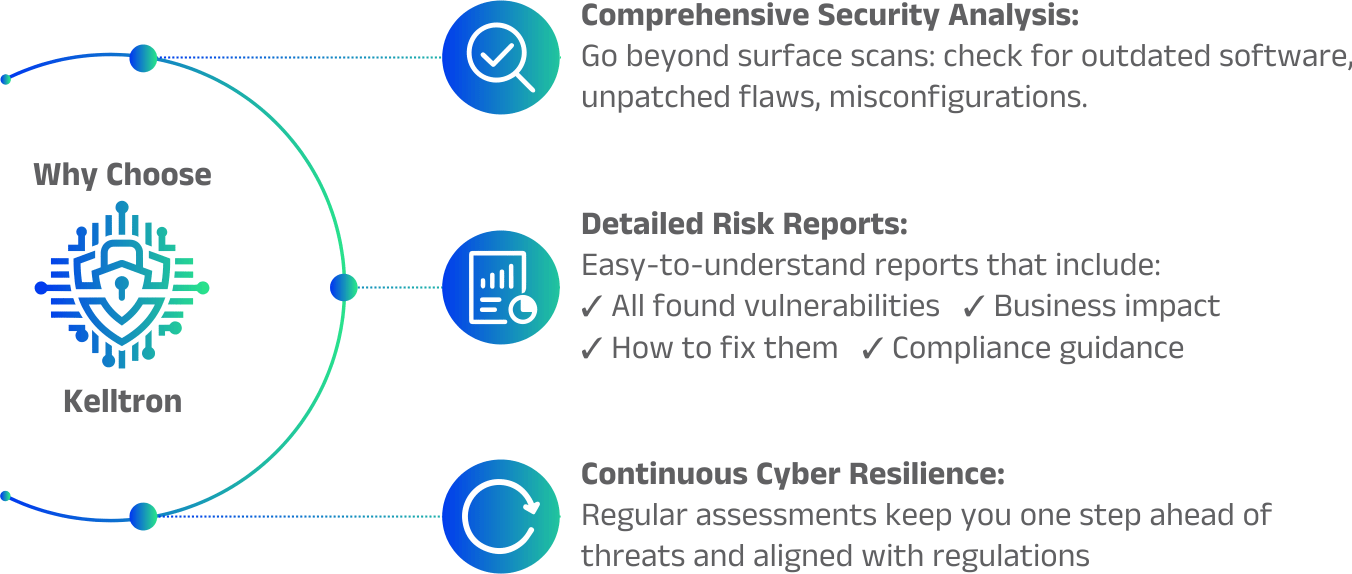
Go beyond surface scans: check for outdated software, unpatched flaws, and misconfigurations.
Easy-to-understand reports that include
Regular assessments keep you one step ahead of threats and aligned with regulations.













