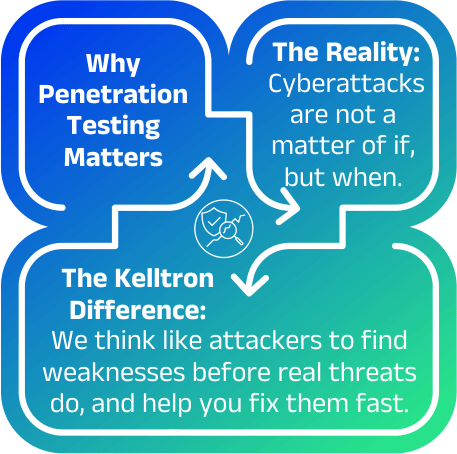
Cyberattacks are not a matter of if, but when.
We think like attackers to find weaknesses before real threats do, and help you fix them fast.
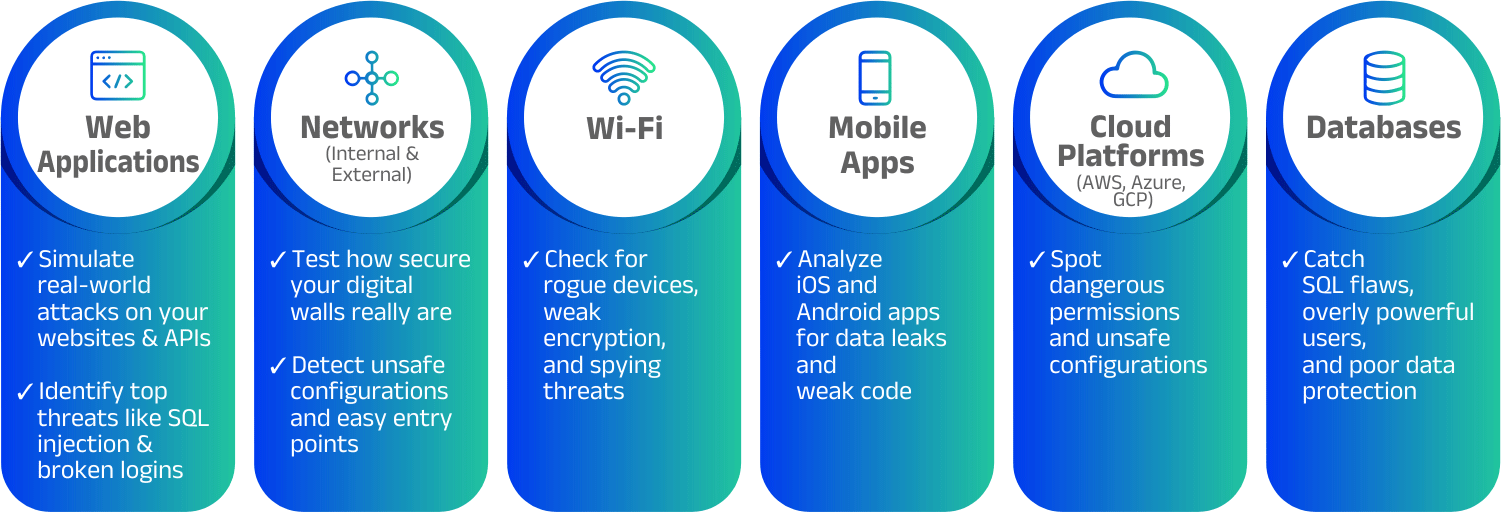
We mimic modern attacker behaviour, not just scan ports.
Faster, deeper, more intelligent vulnerability detection.
Offensive security specialists + Red Team certified experts.
Mapped findings to GDPR, PCI-DSS, HIPAA, and ISO 27001 standards.
Not just problems and solutions you can act on immediately.


Real adversary simulation
Fast, smart, thorough
Certified Red Team professionals
GDPR, PCI, ISO, HIPAA













