X
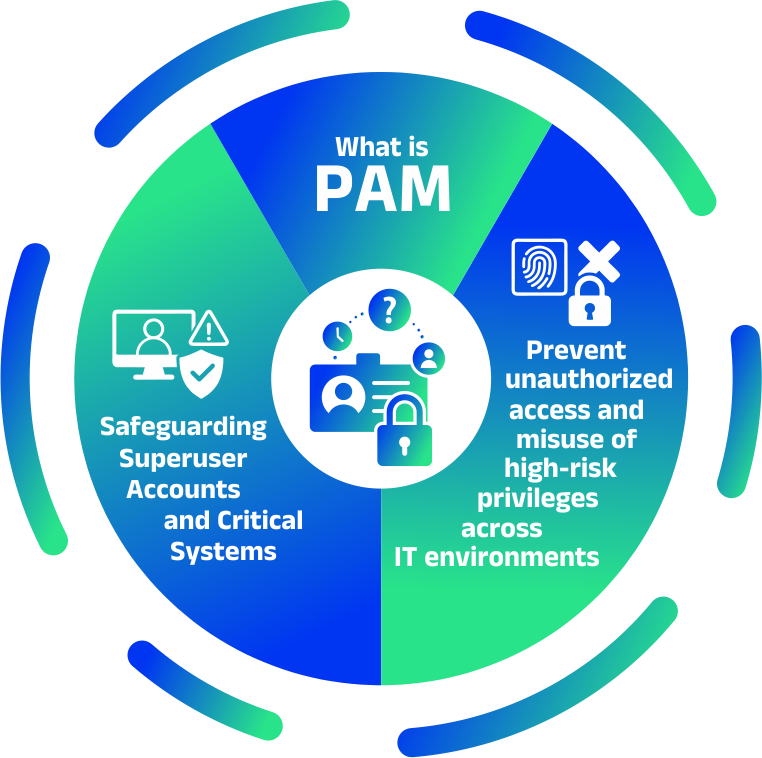
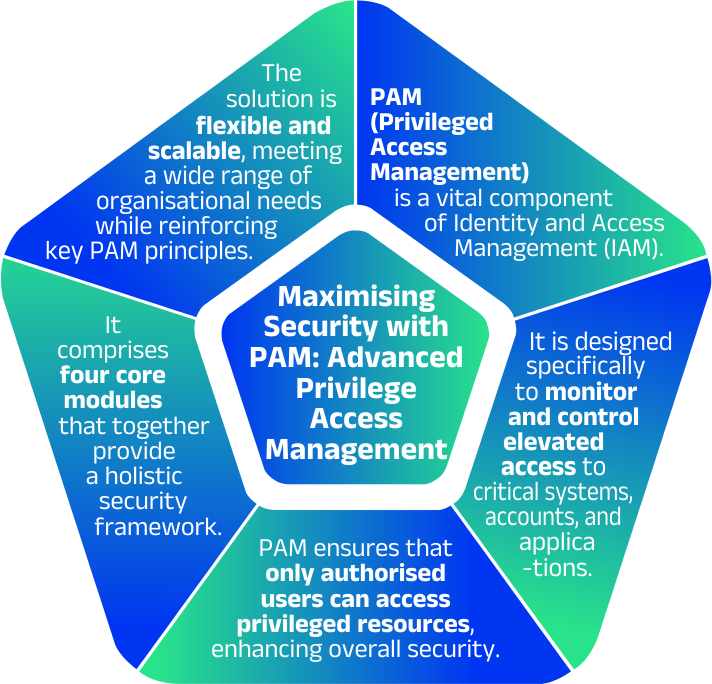
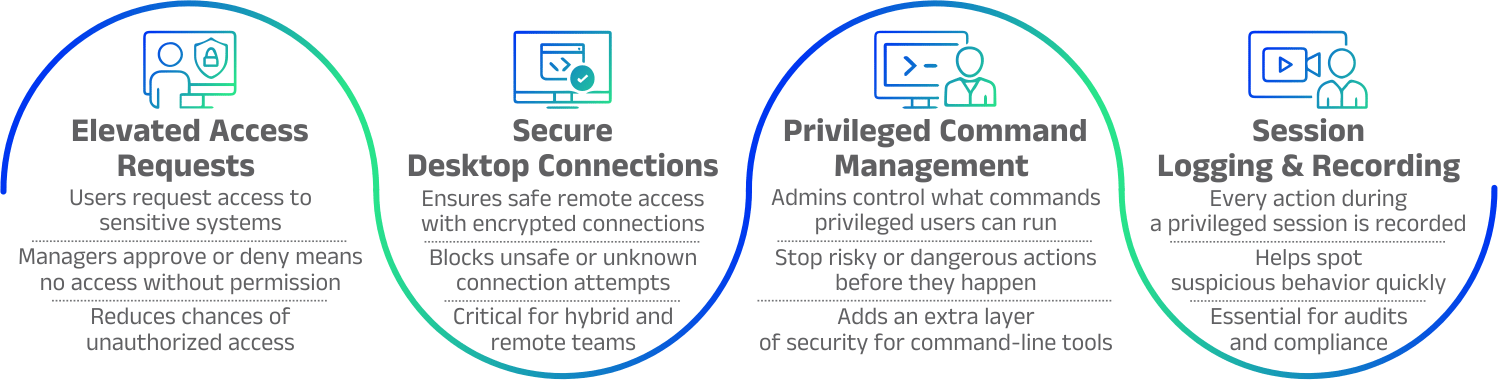
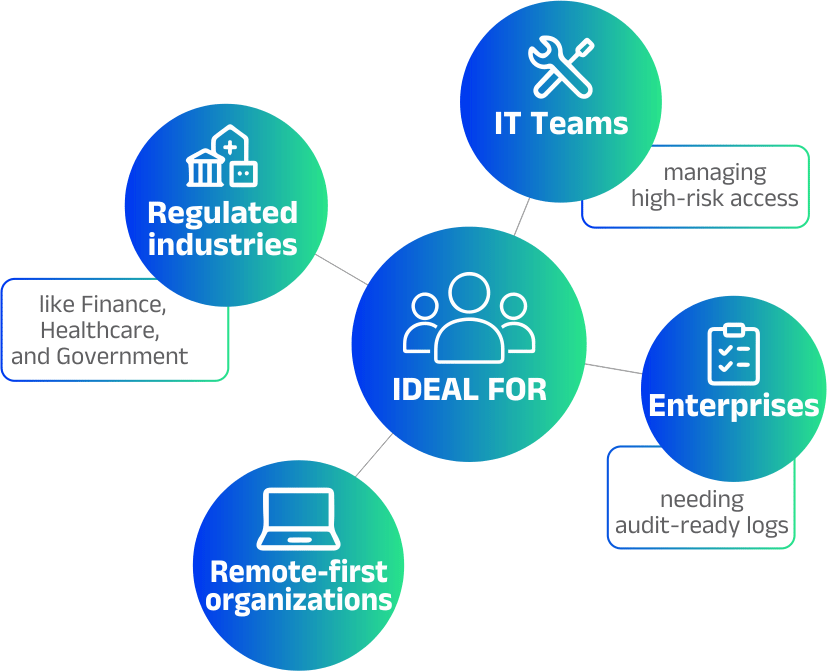
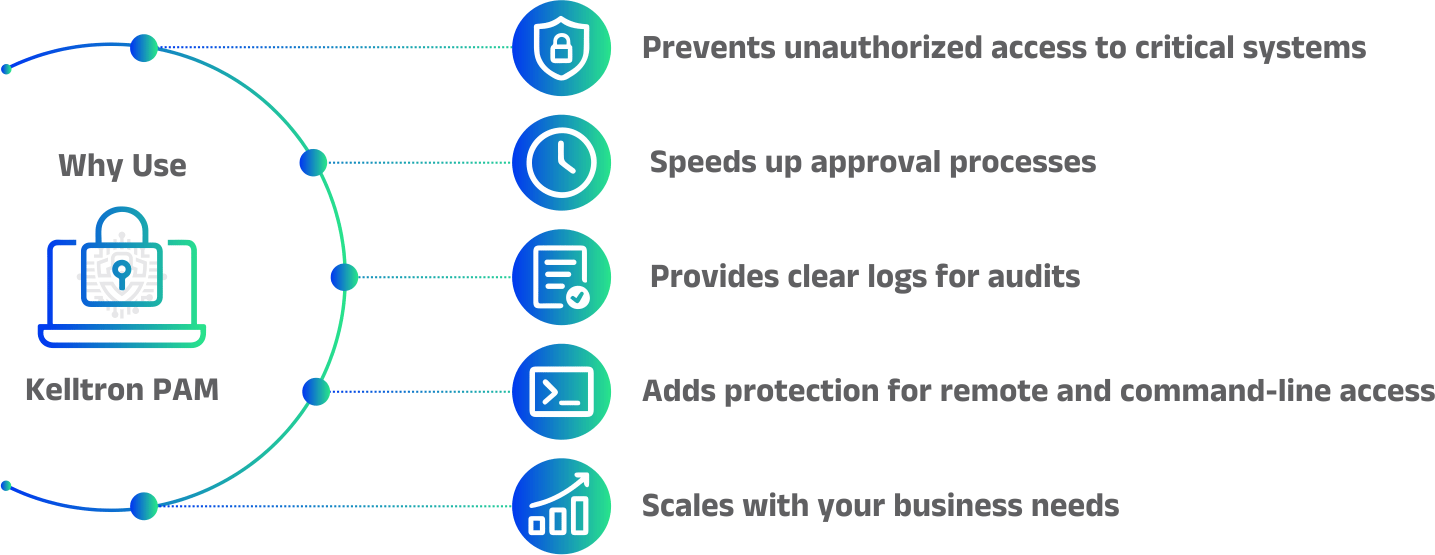
Privileged Access Management (PAM)
Enhance data security with our Data Privilege Access Management tool
Manage sensitive information access effortlessly while automating real-time privilege controls to strengthen security and meet compliance standards.