How Kelltron's IAM Solution Protects Your Business?
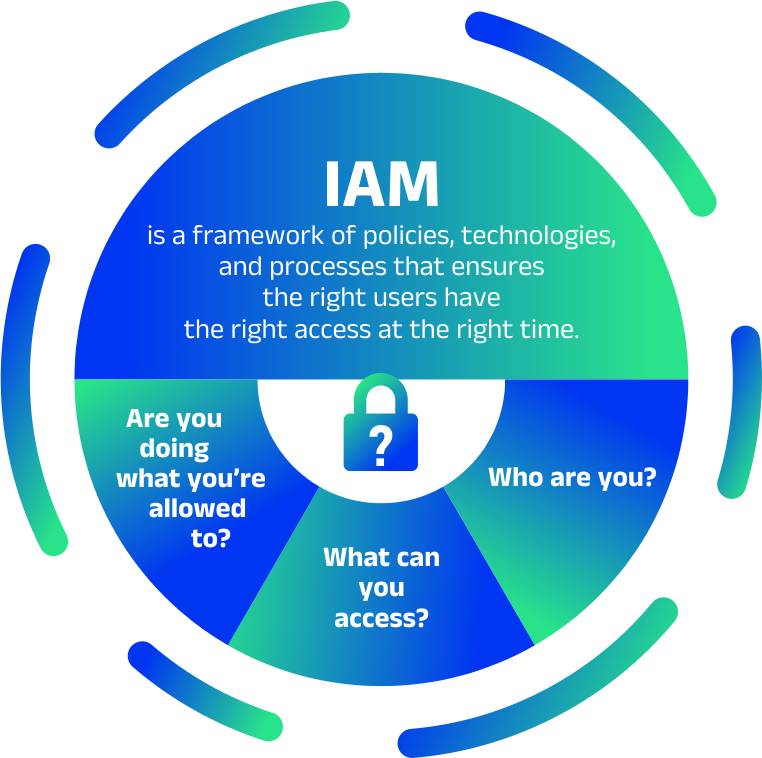
User Identity Verification
Ensure that only legitimate users, employees, contractors, and partners can log in and access resources.
Access Control & Privilege Management
Assign roles and permissions based on the principle of least privilege, reducing overexposure to sensitive data.
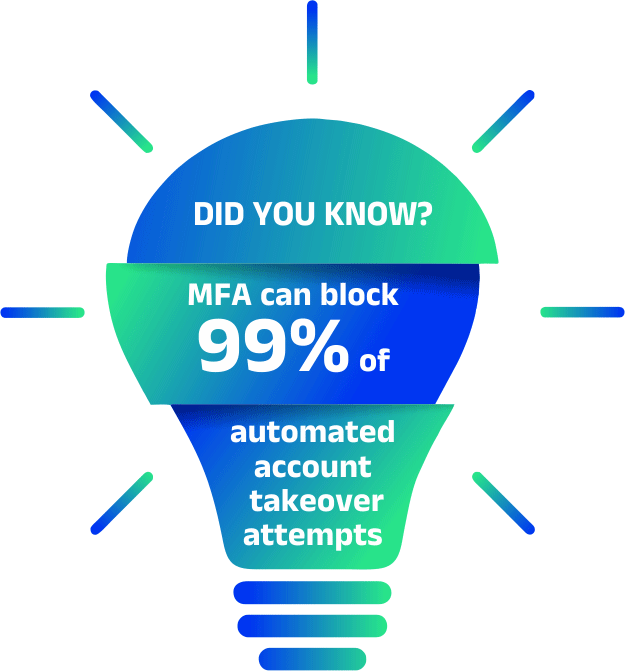
Multi-Factor Authentication (MFA)
Add an extra layer of protection beyond passwords to defend against unauthorised access.
Single Sign-On (SSO)
Simplify user access across multiple systems and applications without compromising security.
Continuous Monitoring & Audit Trails
Track user activity in real time and maintain detailed logs for security and compliance reviews.